analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
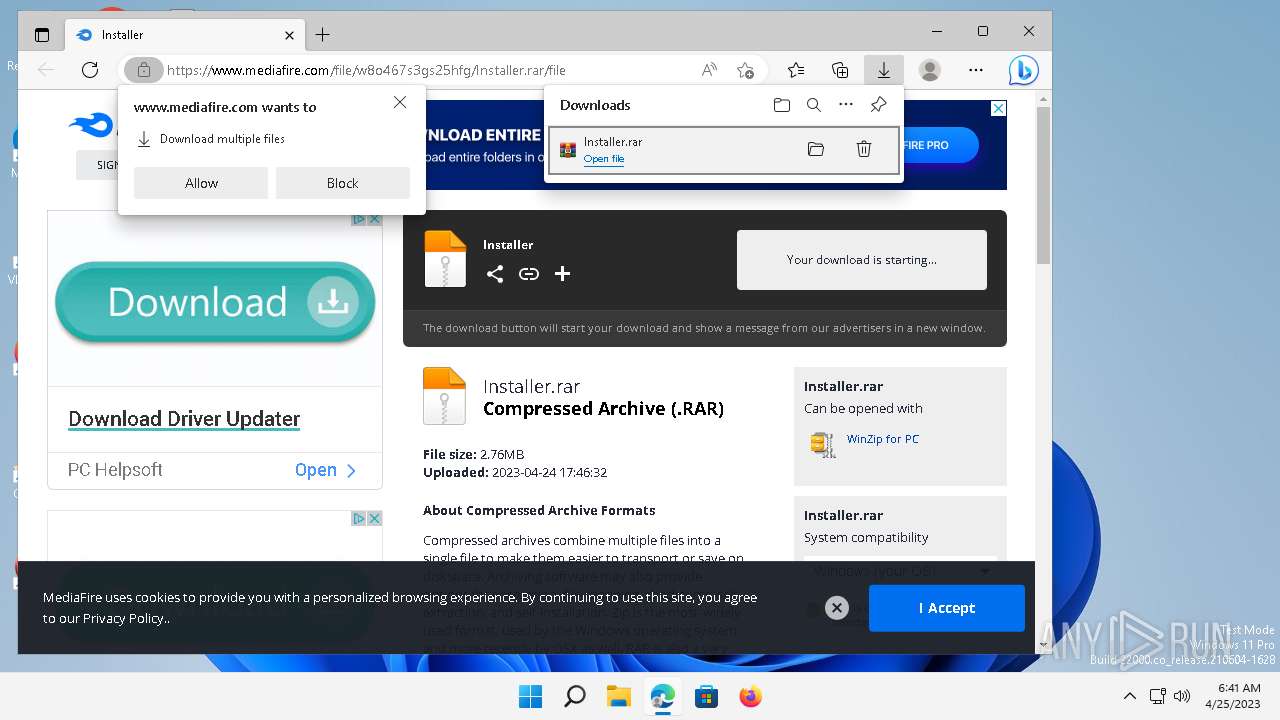
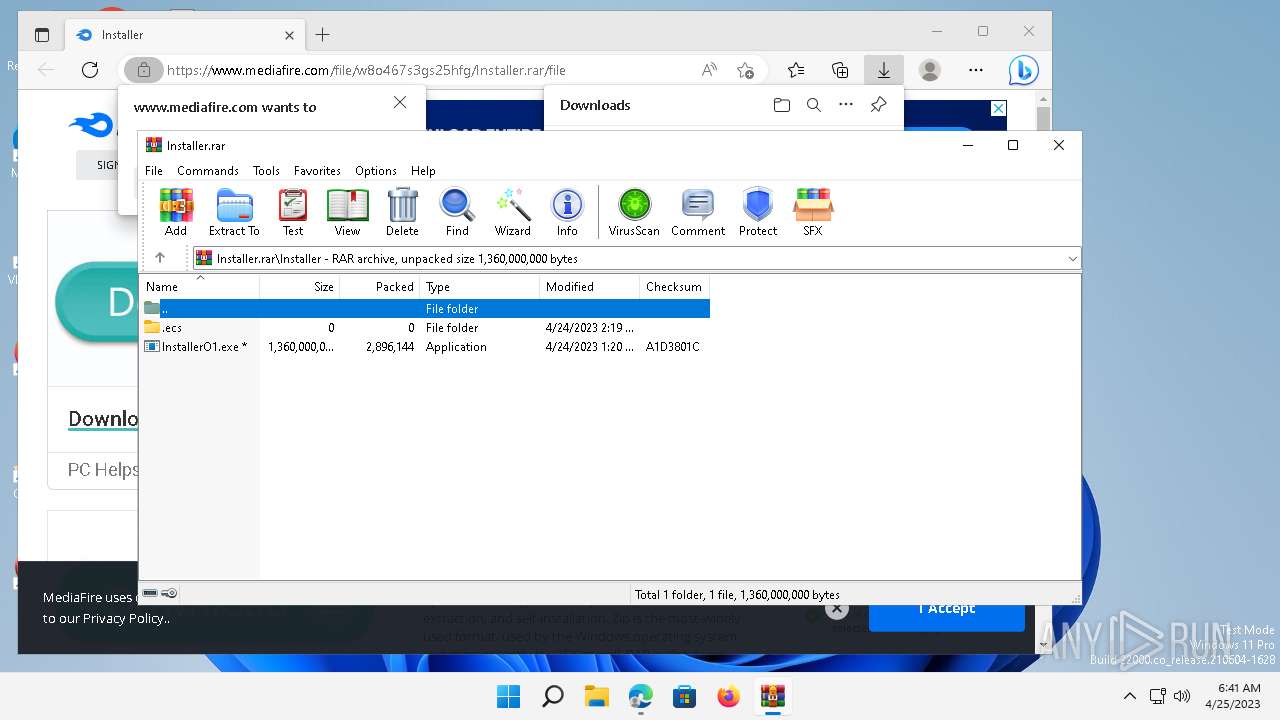
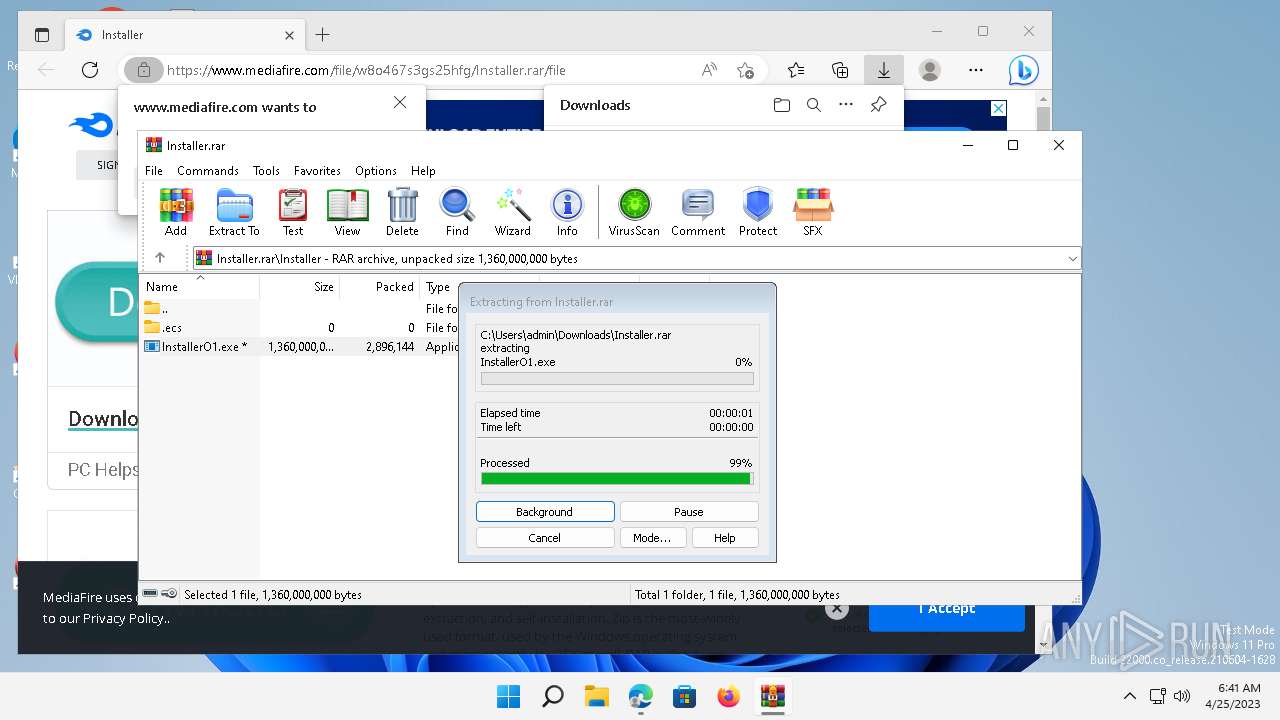
| URL: | https://www.mediafire.com/file/w8o467s3gs25hfg/Installer.rar/file |
| Full analysis: | https://app.any.run/tasks/b56a4f0b-fcf7-4b09-b4fe-647ddc070e3c |
| Verdict: | Malicious activity |
| Threats: | Raccoon is an info stealer type malware available as a Malware as a Service. It can be obtained for a subscription and costs $200 per month. Raccoon malware has already infected over 100,000 devices and became one of the most mentioned viruses on the underground forums in 2019. |
| Analysis date: | April 25, 2023, 13:40:58 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EA571C59B6C91BFE802AE33EDFFE9D9C |
| SHA1: | C0FCD51F6C3982272E4EBA97600A6C0BD2E21F38 |
| SHA256: | A845B5AF33811ED4F767A12C4A8798D42D3F3F0D231F0FA7887293781A6C06E0 |
| SSDEEP: | 3:N8DSLw3eGUouvWWz3iTXLaA:2OLw3eG6vRz3wXLaA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- OpenWith.exe (PID: 7820)
- explorer.exe (PID: 4036)
Reads settings of System Certificates
- explorer.exe (PID: 4036)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7820)
- explorer.exe (PID: 4036)
INFO
Checks proxy server information
- explorer.exe (PID: 4036)
The process checks LSA protection
- explorer.exe (PID: 4036)
- OpenWith.exe (PID: 7820)
Application launched itself
- msedge.exe (PID: 2180)
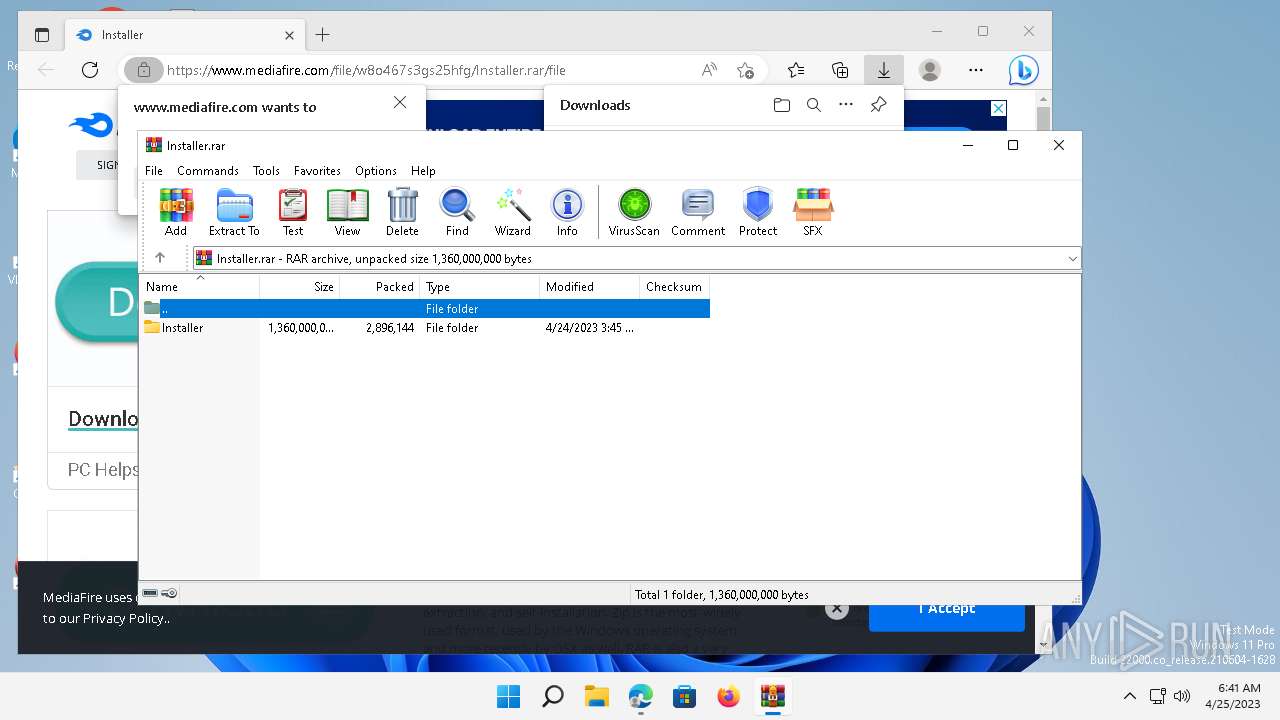
The process uses the downloaded file
- WinRAR.exe (PID: 7588)
- OpenWith.exe (PID: 7820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
156
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://www.mediafire.com/file/w8o467s3gs25hfg/Installer.rar/file" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 7080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=111.0.5563.149 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=111.0.1661.62 --initial-client-data=0x114,0x118,0x11c,0xf0,0x128,0x7ff8fc98b5f8,0x7ff8fc98b608,0x7ff8fc98b618 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 4036 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.22000.184 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7820 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
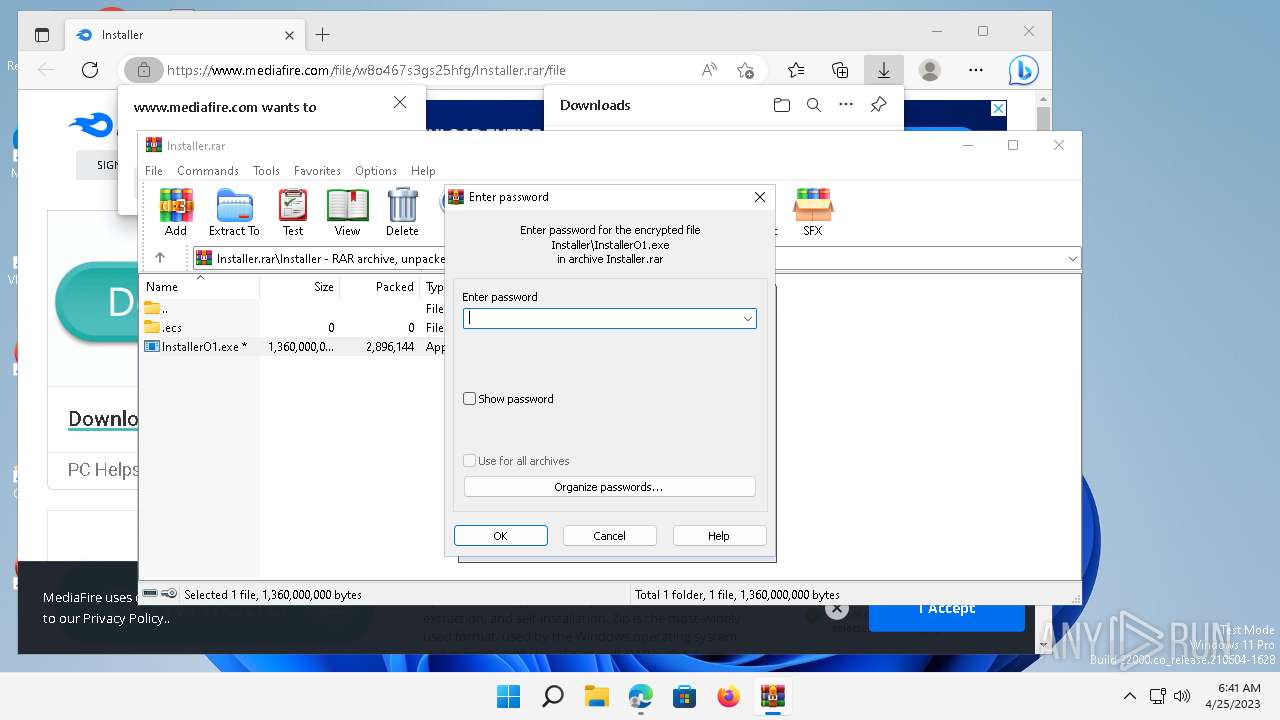
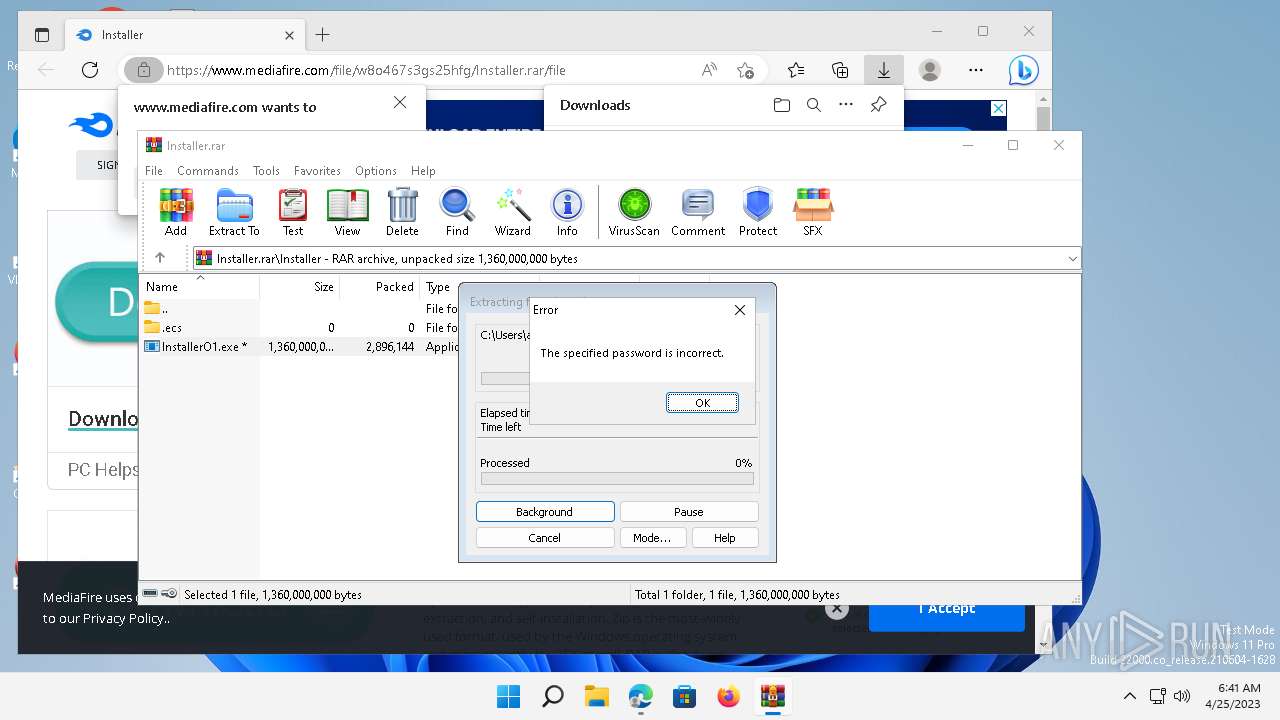
| 7588 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Installer.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 070
Read events
6 948
Write events
116
Delete events
6
Modification events
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2180) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000B0000001C000000ED281000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF809BEF9EA60BD90100000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000710100000A030000C9AC6901540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000B0000001D000000ED281000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF809BEF9EA60BD90100000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000710100000B030000C9AC6901540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | ZFRqtr |
Value: 000000000B0000001D000000E58F1000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF809BEF9EA60BD90100000000 | |||
| (PID) Process: | (4036) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000710100000B030000C1136A01540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000540000006D000000AC912F004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E004500780070006C006F00720065007200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
14
Text files
0
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Installer.rar.lnk | lnk | |
MD5:96259B12552AF37026AB80302ACA474E | SHA256:AEA03C739635E4609EEF6C9A170418A102FEC36C3877DE973AADC0DB5ED79FE6 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\5f7b5f1e01b83767.automaticDestinations-ms | binary | |
MD5:F45368AF6A75F24EC427948F540AA8AF | SHA256:8467CBEF7F953442B28E955D0F6A1C7BE9643455E596DFE246228670591AD5A4 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 7588 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:D2DD4C123F96E53CFE382D3B4130E639 | SHA256:392E99B4C5BF927688342E744086AA9F619394924173C9D97AFD209DB1D9550C | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:821659F12A6955A6811B15D31B08C8B0 | SHA256:193E650E5854EFB302073779A5DE84A8EBF33465703E72BADAE4BDFDFEB32217 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\46f433176bc0b3d2.automaticDestinations-ms | automaticdestinations-ms | |
MD5:DA1798B0AAE4600043EBFEF231C0CBA6 | SHA256:AAF2F802FD63EA273987F939E0CFA1BB3C205937F28DE9371C1E4A5033CB1637 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Downloads.lnk | lnk | |
MD5:406D17EFA6E96B42ECFF687648456546 | SHA256:8FB39D113E284E5E078FE44D5A25DF2ECF45544A6B6B24606D24990BAE3F120E | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:84418143D4EA6C829486C2E0B588D9BB | SHA256:94941FD0417BF809EADC4CDA6234B1C07E8AA8403D2E264858A2747CFBFF02E3 | |||
| 2180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:F08531363BD004D9DA5B6B776D25F336 | SHA256:AC046D56F0CAF974B8A21DB0D7EA48D803A7B31992ECC58397F6C4FDBF869396 | |||
| 4036 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9DB46433D173B274B647CC47A797D94D | SHA256:2A1A2D39AE4454311185A42B9F22FF36157C074E94565A7F6E2E479E60554CB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
133
DNS requests
156
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/vcruntime140.dll | RU | executable | 78.2 Kb | malicious |
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/msvcp140.dll | RU | executable | 438 Kb | malicious |
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/freebl3.dll | RU | executable | 668 Kb | malicious |
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/mozglue.dll | RU | executable | 612 Kb | malicious |
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/nss3.dll | RU | executable | 1.95 Mb | malicious |
— | — | GET | — | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/sqlite3.dll | RU | — | — | malicious |
4036 | explorer.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8e5c859524e94725 | US | compressed | 4.70 Kb | whitelisted |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
6316 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 45.15.156.233:80 | http://45.15.156.233/aN7jD0qO6kT5bK5bQ4eR8fE1xP7hL2vK/softokn3.dll | RU | executable | 248 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1480 | svchost.exe | 13.107.4.52:80 | www.msftconnecttest.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4536 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
4536 | msedge.exe | 20.8.16.139:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4036 | explorer.exe | 13.107.4.50:80 | ctldl.windowsupdate.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4536 | msedge.exe | 138.91.254.96:443 | api.edgeoffer.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6316 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
6316 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4536 | msedge.exe | 104.16.54.48:443 | www.mediafire.com | CLOUDFLARENET | — | suspicious |
6696 | svchost.exe | 23.35.236.109:443 | fs.microsoft.com | AKAMAI-AS | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.edgeoffer.microsoft.com |
| whitelisted |
www.mediafire.com |
| shared |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.msftconnecttest.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
4536 | msedge.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
— | — | Potentially Bad Traffic | ET INFO Commonly Abused Content Delivery Network Domain in DNS Lookup (btloader .com) |
4536 | msedge.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |
4536 | msedge.exe | Potentially Bad Traffic | ET INFO Observed Abused Content Delivery Network Domain (btloader .com in TLS SNI) |
— | — | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
— | — | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
1 ETPRO signatures available at the full report